The basics on malware

The examples are everywhere: In November, wereported that malware was used to steal information about one of Japan's newest rockets and upload it to computers controlled by hackers. Critical systems attwo US power plants were recently found infected with malware spread by USB drives. Malware known as "Dexter" stole credit card data from point-of-sale terminals at businesses. And espionage-motivated computer threats are getting more sophisticated and versatile all the time.Some say we're living in a "post-PC" world, but malware on PCs is still a major problem for home computer users and businesses.
In this second installment in the Ars Guide to Online Security, we'll cover the basics for those who may not be familiar with the different types of malware that can affect computers. Malware comes in a variety of types, including viruses, worms, and Trojans.
Viruses are programs that can replicate themselves in order to spread from computer to computer, while targeting each PC by deleting data or stealing information. They can also change the computer's behavior in some way.
"Almost all viruses are attached to an executable file, which means the virus may exist on a system but will not be active or able to spread until a user runs or opens the malicious host file or program,"Cisco notes. "When the host code is executed, the viral code is executed as well. Normally, the host program keeps functioning after it is infected by the virus. However, some viruses overwrite other programs with copies of themselves, which destroys the host program altogether. Viruses spread when the software or document they are attached to is transferred from one computer to another using the network, a disk, file sharing, or infected e-mail attachments."
Worms are similar to viruses in that they replicate themselves to spread from machine to machine. Cisco says the main difference is a "worm operates more or less independently of other files, whereas a virus depends on a host program to spread itself." Worms spread easily and are likely to cause harm not just to individual PCs but to entire computer networks. One of the most destructive worms ever unleashed on the Internet was dubbed Slammer, which recently marked its 10-year anniversary.
Trojans do not replicate themselves, unlike viruses and worms. They are named after the Trojan horse of ancient Troy because they disguise themselves as legitimate, harmless programs to convince users to install them. "After it is activated, it can achieve any number of attacks on the host, from irritating the user (popping up windows or changing desktops) to damaging the host (deleting files, stealing data, or activating and spreading other malware, such as viruses)," Cisco writes. "Trojans are also known to create back doors to give malicious users access to the system."
Certain types of attacks combine attributes of viruses, worms, and Trojans into "blended threats" that may spread more effectively and be harder to defend against.
In addition to viruses, worms, and Trojans, malware can be divided further into sub-categories such as backdoors, remote access Trojans, information stealers, and ransomware. In his 2012 book "Malware, Rootkits & Botnets: A Beginner's Guide," Security expert Christopher Elisan describes these types of malware:
Backdoors
As their name implies, backdoors let hackers gain sneak attack access to an infected system, bypassing security "through the use of undocumented OS and network functions," Elisan writes. As an example, a backdoor was used to hack into RSA's systems in 2011. This was a targeted attack, gaining a foothold in RSA's network by sending innocent-looking phishing e-mails to workers. The e-mail had a subject line of "2011 Recruitment Plan" and contained an Excel file with an embedded Adobe Flash file that installed the backdoor:
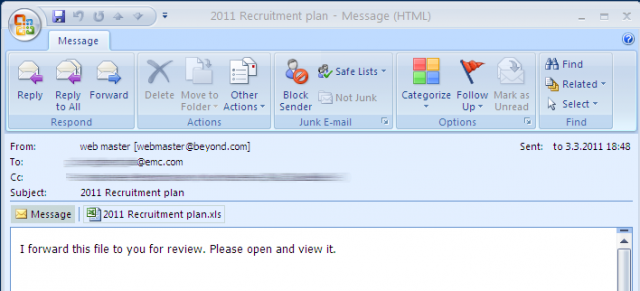
Enlarge / Looks legit, right?
Launching the attachment in Outlook led to the Flash object being executed by Microsoft Excel. By targeting a vulnerability allowing the execution of code, the object dropped a variant of the so-called "Poison Ivy" backdoor onto the RSA computer. Poison Ivy connects back to servers operated by malicious users. "Once the connection is made, the attacker has full remote access to the infected workstation," F-Secure wrote in 2011. "Even worse, it has full access to network drives that the user can access."
Remote Access Trojans
"A remote access Trojan (RAT) is a malicious administrative tool that has backdoor capabilities, enabling an attacker to gain root access to the compromised machine," Elisan writes. "The main difference between a RAT and a traditional backdoor is that the RAT has a user interface, the client component, which the attacker can use to issue commands to the server component residing in the compromised machine."
Thousands of compromised computers can be controlled with remote access Trojans, letting attackers do "almost anything" they want. They can install programs on the infected PC, steal information, or just flat-out destroy the computer.
Information stealers
Diving deeper into malware designed to steal information, Elisan describes keyloggers, desktop recorders, and memory scrapers, which can steal passwords, financial credentials, proprietary data, "or anything that the attackers can use to their advantage or monetize."
A keylogger records the user's keystrokes and "stores them locally for later retrieval, or sends them to a remote server that the attacker has access to." Desktop recorders take periodic screenshots of the desktop, while memory scrapers take information out of a computer's memory while it's being processed. "Data that is processed in memory is unencrypted. This is why this is the best place to grab data," Elisan writes.
Keyloggers can be used for supposedly legitimate purposes, with some companies selling software letting you track the computer activity of family members. This might appeal to parents who want to monitor their children's Internet activity—or to someone who wants to spy on a cheating spouse.
Ransomware

Enlarge / A typical message displayed on a computer infected by ransomware.
Similar ends can also be accomplished by locking the user out of the whole system or threatening destruction of the machine with a Trojan.
Ransomware builds on the annoying tradition of viruses bombarding users with popup ads for fake antivirus products. "Ransomware can be considered the successor of fake antivirus malware as the leading cybercrime threat facing consumers," Trend Micro wrote in a report recapping security in 2012. "Both threats cause users to worry about something (i.e., losing important data or downloading malicious files) and asks them to pay up to make the 'problem' go away."
Source://http://arstechnica.com
No comments:
Post a Comment